LATEST NEWS
Data Sharing Critical to AI’s Use in Cybersecurity Strategies for enabling the effective use of AI technologies in cyber-defense were highlighted by a
Cyber-Attack on Woodland Trust
Cyber-Attack on Woodland Trust A charity that protects and restores woodland in England, Northern Ireland, Scotland, and Wales has been
South Carolina Plans Cyber-Ecosystem
South Carolina Plans Cyber-Ecosystem The University of South Carolina (UofSC) has struck up a partnership with the Palmetto State to
Government Security Supplier Suffers Double Breach A French cybersecurity company with government clients revealed this week that an unauthorized third
Financial Regulator Hit by 240,000 Malicious Emails in Q4 2020 The UK’s financial regulator was bombarded with nearly a quarter
Researchers from TIM’s Red Team Research (RTR) discovered 2 new zero-day vulnerabilities in WordPress Plugin Limit Login Attempts Reloaded Italy
HelpSystems Expands Cybersecurity Portfolio Through Latest Acquisition HelpSystems has announced a new acquisition to further boost its security product offerings.
White Ops Acquired by Goldman Sachs
American cybersecurity company White Ops announced today that it has been acquired by Goldman Sachs’ Merchant Banking Division in partnership with ClearSky Security and NightDragon. Terms of the transaction,
SolarWinds Hackers Aimed to Access Victim Cloud Assets after deploying the Solorigate Backdoor
Microsoft security researchers have continued to investigate Solorigate which caused supply chain compromise and the subsequent compromise of cloud assets
It’s safe to assume that pretty much everyone is ready to move on from 2020. Between the COVID-19 pandemic, political battles, and
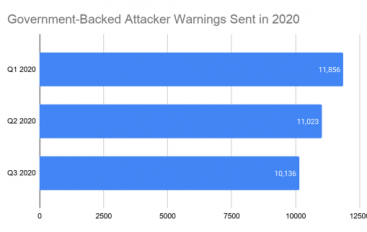
Google delivered over 33,000 alerts to its users during the first three quarters of 2020 to warn them of attacks
Spawn of Demonbot Attacks IoT Devices
Threat researchers have spotted a new kind of cyber-attack that uses a variant of Mirai malware to target a port
Internal culture is a major determinant in how effective organizations’ cybersecurity practices and behaviors, according to a panel discussion at
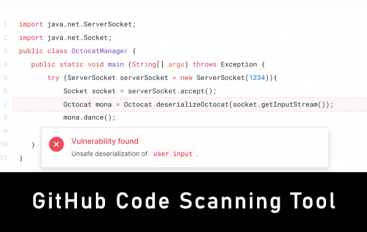
GitHub Launches Code Scanning Tool to Find Security Vulnerabilities – Available for All Users
GitHub launches a new code scanning tool that helps developers to detect vulnerability before the application reaches production. The tool
Researchers at an Israeli operational technology (OT) company have discovered multiple critical vulnerabilities in two popular industrial remote access software
New Toolkit Secures US Teleworkers
The Cyber Readiness Institute (CRI) has expanded its partnership with the US Department of Homeland Security’s Cybersecurity and Infrastructure Security
Kylie Jenner’s makeup company has warned customers that their information may have been compromised in a recently detected security incident
IT Security
Ivanti has announced the acquisitions of mobile device management vendor MobileIron and secure access and VPN provider Pulse Secure. Under
ATM Penetration testing, Hackers have found different approaches to hack into the ATM machines. Programmers are not restricting themselves to
As cybersecurity leaders struggle with a mix of point solutions to defend against a wide range of vulnerabilities and endpoint
TELECOM SECURITY
How to Protect Your Smart Home from IoT Threats?
Our world is increasingly becoming digital as we are moving towards a society that is interconnected through a web of
SOC Analyst Training – Cyber Attack Intrusion Analysis With SIEM Tools | From Scratch To Advanced
SOC Training is one of the most important concern in order to build a Quality Security Operation Center Team to
What is an Indicator of Attack (IOA) IoA’s is some events that could reveal an active attack before indicators of
Industrial & OT Security
In the IoT Ecosystem, Not too long ago in history, the idea that people and objects could be inter-connected would
The Industrial Internet of Things (IIoT) is made up of interconnected sensors, instruments and other devices networked together with ICS/SCADA
SCADA/ICS Dangers & Cybersecurity Strategies
Nearly 60% of surveyed organizations using SCADA or ICS reported they experienced a breach in those systems in the last
CLOUD SECURITY
IT firm Pure Storage has entered into a definitive agreement to acquire Portworx, a Kubernetes data services platform. The deal,
CASB definition Think of cloud access security brokers (CASBs) as central data authentication and encryption hubs for everything your enterprise
Cloud migration is the process of moving applications into the public and private cloud infrastructure to achieve cloud’s agility, resiliency